First time into the world of SSL Certificates; need simple, practical, usable, tips and explanations to implement one, alright then let’s get started. Few concepts:
SSL also known as Secure Socket Layer is a secure protocol which makes http traffic secure i.e. makes it https. It is a transport level protocol, meaning end to end traffic [e.g. from your browser to IIS] is encrypted using Public/Private Key pairs. This is as opposed to message level encryption where each individual Message [SOAP packet] is encrypted.
What is Public/Private Key Pair?
This question could be asked in no: of ways; what is PKI Infrastructure or what is Asymmetric Encryption? The answer is as follows:
Symmetric Encryption (e.g. DES) uses same key at both ends of traffic flow to encrypt and decrypt whereas Asymmetric Encryption uses a Private Key at Server end. A Private Key is secure and sits only on server; consider it the identity of the server. Public key is at the other end of traffic to decrypt and encrypt. Although there are no: of protocols available, SHA1-RSA seems to be a popular cocktail for Asymmetric encryption.
What is a CA?
This could also be asked as what is root authority? Or what is your root? This is really guys like Versign, Thawte, Geocert. Digicert etc. – Clarification: when I say ‘guys’, I mean ‘Digital Certificates’ of these companies. Think of these as the ‘Parent’ or ‘Master’ certificates. These are able to ‘issue’ SSL certificates which you would install on your server. Sometimes these issued certificates aarre able to issue more certificates. This is referred to as ‘Chain’ of certificates By default, our machine contains a no: of these pre-installed ‘Root’ and ‘Intermediary’ certificates.
To get to these pre-installed certificates, go to Internet explorer-->Tools-->Internet Options-->Content-->Certificates .
Here is a screenshot of Trusted Root CAs – i.e. your browser inherently trusts any certificate issued by these CAs. Remember these are Certificates of CAs themselves, i.e. these are certificates which ‘issue’ other certificates.
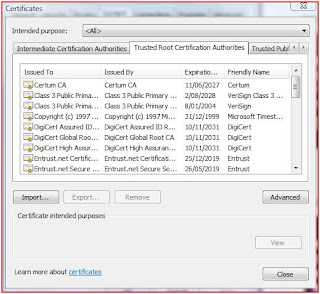
<
Here is another screenshot of the actual certificates installed on your machine. For e.g in the following screenshot, there is a certificate I issued to myself:
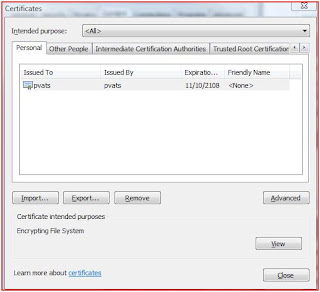
You can also look at certificates using Microsoft management console too. Go to Start-->Run-->type mmc-->File-->Add-Remove Snap-in-->double click Certificates-->Select ’Computer Account’ on ensuing pop-up-->Next-->Finish-->OK. This will show you the following view:
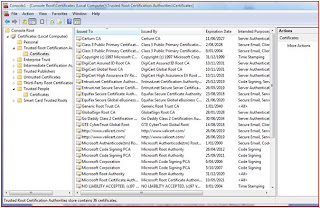
What is a Digital Certificate?
This question could also be asked as – what does a SSL certificate do? Or what does a Server Certificate do? Answers follow:
1. It secures all traffic from one end of traffic [Browser/Server] to other [IIS server] and is installed on a server e.g. a Web Server like IIS. It also contains a Private Key.
2. It is usually issued by a public CA [Certification Authority] like Verisign, Thawte etc but it can also be issued by an inbuilt CA in our local machine – a web server or even a XP/Vista Machine.
3. Digital certificate can be used for :
A) Transport Level: End to end authentication whereby the browser establishes session key with the web server and the encrypted session key is used for the duration of the session; all data passed between client and server is encrypted. e.g. ebay, paypal and your bank’s net banking services.
B) Authentication: If the server has a SSL certificate installed, then the client browser connects to the server and as the server responds to the client, it authenticates itself to the client; confirming it is who it claims to be. E.g. Company A. There are 2 levels of authentication provided by the SSL certificate:
i) Domain Authentication: Just the domain name is verified i.e. if someone connects to your server; the browser is guaranteed it is connecting to “www.yoursite.com”. The guarantee is provided by the issuer (e.g. Verisign)
ii) Organisation Authentication: The fact that Company A owns “www.yoursite.com” is verified. This is true SSL certificate and this si what you would want for your web server.
C) Mutual Authentication: This is a special case of Authentication. Imagine there are 2 web servers and both of them are required to authenticate/identify to teach other e.g. Company A’s Server A when initiates traffic flow with Company B’s Server B, the SSL certificate is requested from Server B and when Server B responds it asks Server A for its certificate.
In the next article on this series, I will discuss how to create and Install SSL certificates – in development and Production environment. Any suggestions, corrections or comments are welcome.